In a recent report, Sophos X-Ops, a leading cybersecurity company, has sounded the alarm on a new wave of malware attacks using social engineering techniques. Dubbed the “Inhospitality” malspam campaign, this targeted assault is specifically aimed at the hotel industry. The attackers are using cleverly crafted emails, disguised as complaints or requests for information, to gain the trust of unsuspecting hotel staff. These emails contain deceptive links to seemingly harmless documentation, which in reality are malicious payloads ready to steal passwords. The attackers employ various subject lines and scenarios to lure their victims, making it difficult to spot the danger. To further evade detection, the malware is concealed within compressed, password-protected files. This wave of attacks involves the Redline Stealer or Vidar Stealer families of malware, with over 50 unique samples already discovered by Sophos X-Ops. The malware connects to a Telegram chat room for command-and-control. Fortunately, Sophos’ endpoint security products are equipped to detect this malware under the name Troj/Agent-BKJE. Stay vigilant and ensure that your organization is well-protected against these malicious intrusions.
Sophos X-Ops warns of password-stealing malware attack using social engineering
Sophos X-Ops, a leading cybersecurity firm, has issued a warning about a new and sophisticated malware attack targeting the hotel industry. This password-stealing malware utilizes social engineering techniques to trick hotel staff into downloading and executing malicious payloads, putting sensitive customer information at risk.
This image is property of news.sophos.com.
Inhospitality malspam campaign targets hotel industry
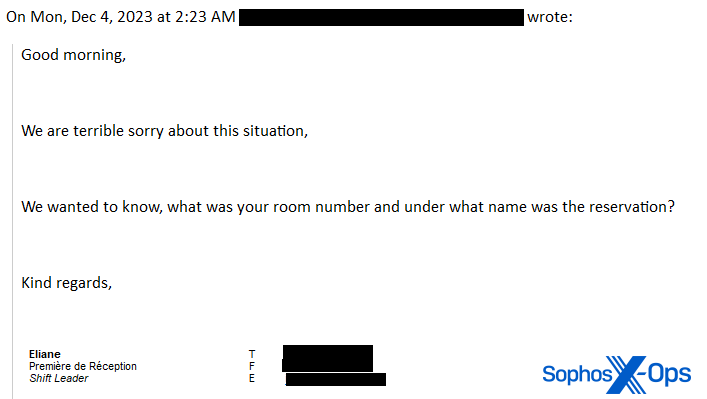
Dubbed the “Inhospitality” malspam campaign, this attack specifically targets the hotel industry. Attackers are sending emails to hotel staff members, disguising themselves as hotel guests with complaints or requests for information. By posing as legitimate customers, the attackers aim to gain the trust of the hotel employees, making them more likely to click on the malicious links within the emails.
Attackers send emails with complaints or requests for information to gain trust
To gain the trust of hotel staff, the attackers employ social engineering tactics by sending emails that appear to be from disgruntled or concerned hotel guests. These emails contain complaints, requests for information, or false claims of misrepresented charges. By targeting the employees’ desire to provide good customer service and resolve issues, the attackers increase the likelihood of their emails being opened and the links being clicked.
This image is property of news.sophos.com.
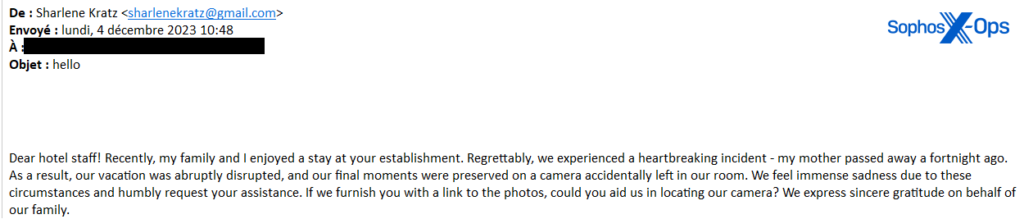
Emails contain links to malicious payloads disguised as documentation
The malicious emails sent in this campaign contain links that appear to lead to documentation related to the guest’s complaints or requests. However, these links actually lead to malicious payloads disguised as legitimate files. Once the unsuspecting hotel staff member clicks on the link and downloads the file, the malware is executed on their system, compromising the security of the hotel’s network.
Attackers use various email subjects and scenarios to lure hotel staff
To increase the success rate of their attack, the attackers use a variety of email subjects and scenarios to lure hotel staff members into clicking on their malicious links. Subject lines may include phrases such as “Urgent Complaint,” “Billing Discrepancy,” or “Reservation Information.” By creating a sense of urgency or intrigue, the attackers aim to grab the attention of the hotel staff, making them more likely to click on the links.
This image is property of news.sophos.com.
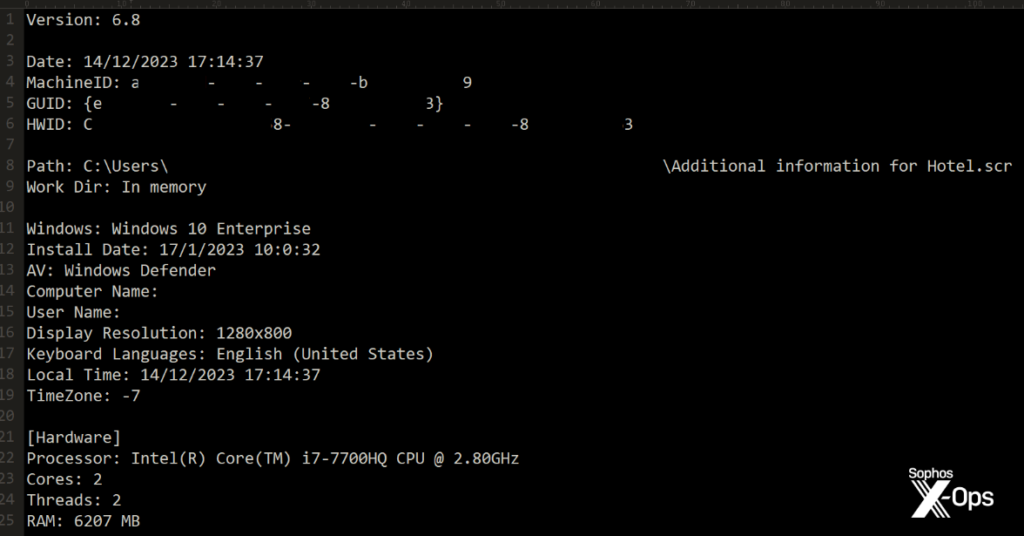
Malware payloads are compressed and password-protected to evade detection
The malware payloads used in this attack are both compressed and password-protected to avoid detection by antivirus software. The attackers utilize techniques to obfuscate the malware’s code and compress it into a smaller file size. Additionally, the files are password-protected to further hinder analysis by security software. These tactics make it challenging for traditional malware detection methods to identify and neutralize the malware.
Malware variants belong to Redline Stealer or Vidar Stealer families
Sophos X-Ops has determined that the password-stealing malware used in the Inhospitality malspam campaign belongs to either the Redline Stealer or Vidar Stealer families. These families of malware specialize in extracting and exfiltrating sensitive information, such as passwords and personal data. Once the malware is executed on a victim’s system, it silently collects and transmits this valuable information to the attackers.
This image is property of news.sophos.com.
Malware connects to a Telegram chat room for command-and-control
In order to maintain control over the infected systems and receive stolen data, the malware establishes a connection to a Telegram chat room for command-and-control purposes. By utilizing a popular messaging platform like Telegram, the attackers can easily communicate with the malware and issue commands remotely. This provides them with the ability to remotely execute additional malicious actions and exfiltrate stolen information.
Sophos X-Ops has discovered over 50 unique samples of the malware
The cybersecurity experts at Sophos X-Ops have identified and analyzed over 50 unique samples of the password-stealing malware used in the Inhospitality malspam campaign. This significant number of samples suggests that the attackers behind this campaign are highly motivated and actively seeking to compromise the security of hotels and their guests. With each new sample, the attackers may be improving their tactics and evading detection.
This image is property of news.sophos.com.
Sophos endpoint security products detect the malware as Troj/Agent-BKJE
Sophos endpoint security products are at the forefront of protecting organizations from such password-stealing malware attacks. The security firm’s advanced detection capabilities have enabled them to identify the specific malware variant used in the Inhospitality malspam campaign as Troj/Agent-BKJE. This identification allows them to provide customers with the necessary tools and updates to defend against this particular threat.
In conclusion, the Inhospitality malspam campaign serves as a stark reminder of the ever-evolving tactics employed by cybercriminals to exploit vulnerabilities in organizations. The hotel industry, in particular, must remain vigilant and educate their staff about the dangers of social engineering attacks. By implementing robust cybersecurity measures, regularly updating software, and partnering with reliable security providers like Sophos X-Ops, hotels can mitigate the risk posed by password-stealing malware and protect their customers’ sensitive information.
