In a recent incident, a blockchain developer named Murat Çeliktepe found himself caught in an elaborate scam after being approached on LinkedIn for what seemed to be a legitimate job opportunity. The recruiter presented an Upwork job posting and asked Çeliktepe to download npm packages from GitHub as part of the job interview. However, a few hours later, Çeliktepe discovered that his MetaMask wallet had been emptied, with over $500 stolen. This distressing experience highlights the need for web developers to remain cautious when dealing with job offers on professional platforms, and serves as a reminder to take necessary precautions to safeguard against potential scams.

This image is property of www.cointrust.com.
Blockchain Developer Falls Victim to Elaborate Scam via LinkedIn Job Offer
In a recent incident, a blockchain developer, Murat Çeliktepe, shared a distressing experience over the holidays after being approached on LinkedIn for what appeared to be a legitimate web development job. The “recruiter” presented an Upwork job posting, seemingly offering a genuine opportunity, and requested Çeliktepe to download npm packages from GitHub as part of the job interview. However, hours later, the developer discovered his MetaMask wallet had been emptied, with over $500 siphoned off.
LinkedIn Encounter Turns Costly
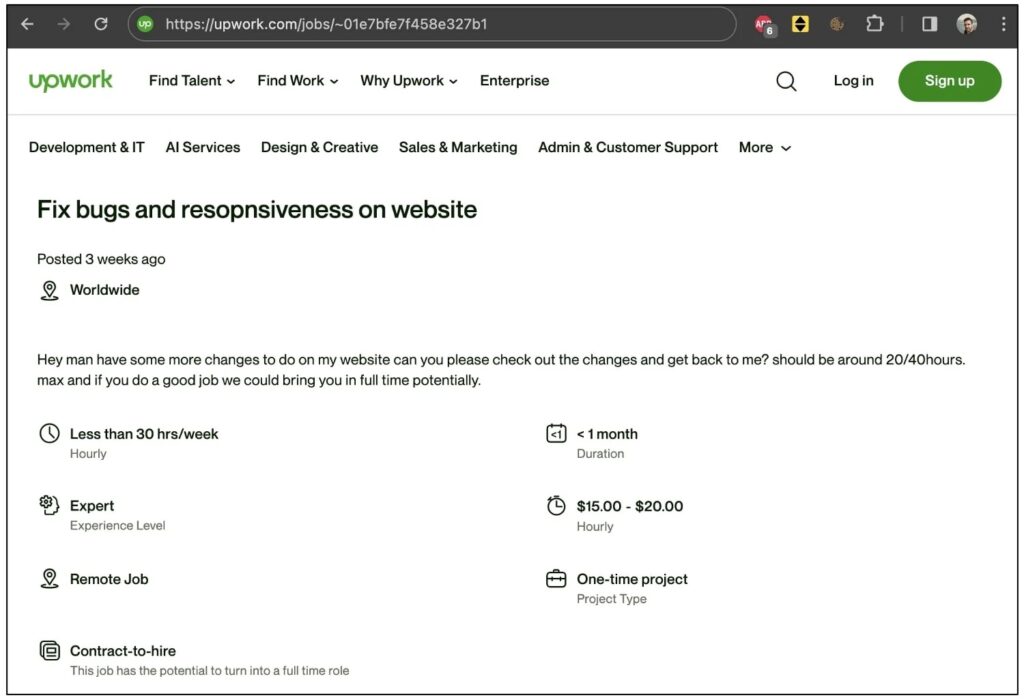
Çeliktepe, based in Antalya, detailed how the LinkedIn recruiter lured him with an Upwork job posting, asking him to fix bugs and enhance website responsiveness. Despite the seemingly authentic nature of the job, the developer’s MetaMask wallet fell victim to a sophisticated attack after downloading npm packages for the “tech interview.”
Challenges in Identifying the Attack Vector
As Çeliktepe shared his ordeal on social media, he sought assistance from the community to understand the mechanics of the attack. Despite examining the code in the GitHub repositories, he remains uncertain about how his MetaMask wallet was breached. Concerningly, even without keeping the MetaMask Secret Recovery Phrase on his computer, the attack resulted in a drained Ethereum balance.
Community Response and Proposed Theories
The developer’s appeal for help attracted both genuine community members and opportunistic crypto bots offering support. Some community insights suggested the npm projects executed by Çeliktepe may have enabled the attacker to deploy a reverse shell, opening up potential vulnerabilities on the developer’s machine.
Widespread Targeting by the Same “Recruiter”
Notably, Çeliktepe is not alone in falling prey to this scheme. Other developers, including security researcher Bartu Bozkurt and Mehmet Selim, reported similar LinkedIn approaches from the same “recruiter.” Bozkurt labeled it a “very well-known type of hack,” indicating a systematic and targeted effort to exploit unsuspecting web developers and security researchers.
Caution for the Community
The incident serves as a stark reminder for web developers and security researchers to remain vigilant against fraudulent job offers on professional platforms. Completing any take-home job exercises on a separate (virtual) machine, detached from the primary device, is recommended as a precautionary measure to safeguard against potential scams. As the community grapples with understanding the intricacies of this elaborate attack, collective awareness and caution become crucial to thwart such malicious schemes.
Çeliktepe’s Experience with LinkedIn Recruiter
Murat Çeliktepe, a blockchain developer based in Antalya, recently encountered a harrowing situation after responding to a LinkedIn job offer. The recruiter, presenting himself as a legitimate recruiter on the platform, posted a job opportunity on Upwork that seemed genuine. Çeliktepe was asked to fix bugs and enhance website responsiveness, tasks commonly associated with web development. However, what appeared to be a legitimate job interview turned out to be an elaborate scam, leading to the theft of funds from Çeliktepe’s MetaMask wallet. This unfortunate incident sheds light on the need for caution when pursuing job opportunities online.
The Mechanics of the Attack
After agreeing to the job interview, the recruiter instructed Çeliktepe to download npm packages from GitHub as part of the evaluation process. npm packages are commonly used in web development projects and are trusted sources for code libraries. However, in this case, the packages contained malicious code that compromised Çeliktepe’s MetaMask wallet. The specific details of how the attack was executed remain unclear, as Çeliktepe enlisted the help of the community to understand the attack vector.
The Role of npm Projects in the Attack
The npm package ecosystem is vast and widely used by developers worldwide. While the majority of packages are legitimate and safe to use, incidents like Çeliktepe’s demonstrate that malicious actors can exploit this trust. By incorporating malicious code into seemingly innocent packages, scammers can gain access to developers’ systems and compromise their digital assets. It is crucial for developers to exercise caution when integrating third-party code into their projects and to verify the authenticity and security of npm packages before use.
This image is property of www.cointrust.com.
Similar Cases of Scam
Çeliktepe’s experience is not isolated. Other individuals, including security researcher Bartu Bozkurt and Mehmet Selim, have reported similar encounters with the same LinkedIn recruiter. This pattern suggests a systematic approach to targeting web developers and security researchers, exploiting their trust in professional platforms like LinkedIn. It is essential for the community to remain vigilant and share information to prevent further victims from falling prey to this scam.
The Scope of the Scammer’s Tactics
The use of LinkedIn as a platform for carrying out fraudulent activities highlights the need for continuous scrutiny in the hiring process. Scammers may use various tactics such as impersonating reputable companies, creating fake job postings, or even leveraging genuine job listings to gain victims’ trust. By utilizing social engineering techniques and taking advantage of individuals’ eagerness to secure employment, scammers can exploit their victims financially and compromise their personal information. It is crucial for job seekers to verify the legitimacy of recruiters and job offers before proceeding with any further steps.
Vigilance against Fraudulent Job Offers
The incident involving Çeliktepe serves as a wake-up call for the web development and security research communities. Given the increasing number of individuals pursuing careers in these fields, scammers see an opportunity to exploit their skills and knowledge for financial gain. Aspiring developers and researchers must exercise caution when presented with job opportunities and thoroughly vet recruiters and platforms before engaging further.
Precautionary Measures for Web Developers and Security Researchers
To protect themselves from falling victim to fraudulent job offers, individuals should adopt the following precautionary measures:
-
Verify the legitimacy of the recruiter: Conduct research on the recruiting individual or organization to ensure they are reputable and have a legitimate online presence.
-
Beware of suspicious requests: Be cautious of recruiters who ask for sensitive information, such as personal identification documents or access to sensitive systems, during the initial stages of the hiring process.
-
Use separate machines for testing and evaluation: Whenever possible, use a separate (virtual) machine to perform job-related tasks, such as downloading and running code, to mitigate the risk of compromising personal or sensitive information.
-
Stay informed about scam tactics: Stay updated on the latest scam tactics targeting web developers and security researchers. Engage with the community, participate in forums, and share information to collectively combat fraudulent activities.
By adopting these precautionary measures, individuals can minimize their exposure to scams and protect their digital assets and personal information.

This image is property of www.cointrust.com.
Conclusion
The incident involving Murat Çeliktepe serves as a cautionary tale for the web development and security research communities. It highlights the need for continual vigilance and skepticism when pursuing job opportunities on professional platforms like LinkedIn. As scammers become increasingly sophisticated in their tactics, it is crucial for individuals to prioritize their online security and take precautionary measures to avoid falling victim to fraudulent job offers. By sharing information and raising awareness within the community, collective protection can be achieved, ultimately minimizing the prevalence of such scams. The road to a secure and trustworthy online job market begins with individual caution and collective vigilance.
